Corporate SaaS environments are intricate ecosystems with complex configurations, ownership, and access patterns. It's quite a task to oversee the configurations required for a strong security posture. Studies show that over 65% of workplace SaaS apps are unsanctioned. Well, hello, the notorious shadow IT phenomenon posing risks to data security, compliance, and overall organizational integrity. Effective user management in SaaS applications can help you tame the risks.

Overcode experts bring you a straightforward, fact-based guide featuring SaaS management best practices. We’ll discuss SaaS permissions management, show you how to optimize your workflows and help you maintain top-tier security. So, let’s get started with smarter and safer SaaS user management.
What is SaaS user management?
User management in SaaS applications involves administering user accounts, access levels, and permissions. This pleiad of measures, practices, and tools helps you properly control software usage and secure online collaboration while securing user data and supporting personalized experiences.
What are the goals of SaaS user management?
User access must be secure, organized, and efficient – these are the most important goals when managing SaaS applications. You can sleep easy when the right people have the correct permissions, security risks are minimized and shadow IT doesn't cause chaos. That’s what you get with the right SaaS user management:
Operational efficiency. A global SaaS spending survey shows that 32% of IT professionals see SaaS automation platforms as an enabler for operational efficiency, helping them free up time for strategic work. The high level of automation in tasks such as user provisioning, access control, and subscription management for local users and groups cuts administrative overhead and optimizes resource allocation.
Simplified compliance. GDPR, CCPA, HIPAA, or SOC 2 are well-known abbreviations for companies handling customer data. But compliance doesn’t stop there. Newer regulations, such as CISA BOD 25-01, highlight the increasing focus on cybersecurity and infrastructure resilience. The regulatory landscape is evolving faster than we think. Organizations must incorporate compliance requirements into their SaaS administration to protect sensitive data and be prepared for audits.
User insights and analytics. User management SaaS tools give you data-based answers: Which apps do your teams rely on most? Which features do they value? Where do they need IT support? Centralized user management applications with built-in user lifecycle reports, user activity monitoring, or anomaly detection can tell you when to remind users about security risks and offer them tech support.
Guaranteed security. The top three SaaS-related concerns of organization leaders for 2025 relate to:
Unsanctioned apps that store sensitive data (34%)
Sensitive files shared publicly (34%)
Not knowing where sensitive data exists (31%)
Managing SaaS applications includes various identity and access management (IAM) solutions and security measures that help business leaders have fewer reasons for security concerns.
How does SaaS user management work?
A properly designed SaaS user management framework allows you to effectively control, monitor, and secure user access across all the cloud-based applications. SaaS management best practices involve creating user profiles, assigning roles, and managing permissions. This means defining who can access which application and what actions they can perform.
Let’s break it down.
User access control types: RBAC vs. ABAC vs. PBAC

We compare the most common access control options to help you choose the best access control model for your organization or application. Objects of interest are each model's applicability, strengths, and weaknesses.
Three common SaaS access management approaches you can follow are:
Role-based access control model (RBAC)
Attribute-based access control model (ABAC)
Permission-based access control model (PBAC)

So, let’s find out exactly how each approach to user access management can help you strike a balance between security and operational efficiency.
What is RBAC?

Role-based access control (RBAC) model allows you to manage user access by assigning specific roles based on the user’s job functions. Each role comes with a set of permissions, granting access to specific resources or actions according to their responsibilities. In RBAC, roles are fixed, so every user in the same role has the same access level. If someone needs more privileges, they get an extra role for more restricted access instead of custom permissions.
Roles in a SaaS company should be regularly checked to confirm that no single user has more privileges than they actually need.
What is ABAC?

Under attribute-based access control, user access is granted or denied based on specific attributes rather than predefined roles. These attributes can include:
User attributes like job title, department, or security clearance.
Environment attributes like time of day, user’s access location, or network connection.
Resource attributes are tied to the specific characteristics of the object being accessed. For example, if we consider a storage system as an object, resource attributes could include storage account name, container name, namespace configuration, file type, etc.
How is ABAC implemented?
For instance, when a user logs into a cloud service with their credentials, the system will retrieve their profile attributes, such as roles or permissions. It will then examine resource attributes like file type, ownership, and sensitivity. Next, it will consider factors like the time of access, the user's location, and whether they are accessing the service through a secure network.
After evaluating all these attributes against established security policies, the system will decide whether to grant access or deny it.
What is PBAC?

Another approach considered among SaaS user management best practices is policy-based access control, which suggests considering users' business roles in combination with the organization’s policies. Such a combination allows us to determine what access privileges users of each role should have.
For instance, a developer may have access to the codebase, but only if they are working during approved hours and connected to the company’s secure network, as defined by internal development policies.
If the question "What is user access management?" still keeps you wondering, here is a comparison table highlighting how access management models differ in flexibility, security, and ease of implementation:

The ‘user' aspect in the question: What is user management?
Access control models are central to effective SaaS user management. However, the way you handle user-related aspects within these models determines the efficiency and security of the entire system. In the following, we look at which aspects need to be considered.
User profile
User profiles, the central elements in SaaS application management, store details of a user’s personal data within the organization – name, job title, department, and contact information. They can also contain user preferences such as language or notification settings and organizational details that define the user’s role and responsibilities.
A good practice is to keep user profiles up to date and integrate them with identity management systems (e.g. Okta or Microsoft Active Directory). When users change roles or departments, the software automatically adjusts their access rights, reducing the risk of unauthorized access or errors.
User role
Roles define which access rights a user has within the SaaS application, depending on their:
Function, i.e. the specific tasks for which a user is responsible, e.g. coding, testing, or managing development plans.
Team/department/organization, i.e. belonging to teams such as frontend, backend, QA, DevOps, etc., or working in the finance or marketing department.
For example, users with the “Developer" role can have authorization to access and modify the codebase. At the same time, users with the “Project manager” role can have access to project management tools and team performance data.
User permissions
Permissions control which actions a user can perform within the SaaS application. They can be assigned directly (PBAC), via roles (RBAC), or dynamically (ABAC). Permissions are the most basic level of access and determine whether a user can read, write, or change different parts of the application.
User groups
By grouping users based on common attributes such as their role, specific departments or teams, external contractors, or not, administrators can apply access rules to multiple users simultaneously.
For example, a "QA" group could have access to test environments and bug-tracking tools, while a "Management" group could have access to project dashboards.
Policies
User management policies define who can access what data, session management, and when additional security measures such as two-factor authentication are required. Many policies are tied to compliance with external regulations.
For example, a policy may block access to sensitive data from outside the corporate network, enforce automatic logouts after inactivity, or require additional authentication for financial transactions.
B2B SaaS application user roles and permissions handling
A well-defined access control SaaS strategy can also be based on data management practices such as segregation. Data segregation helps reduce security risks without impacting operational efficiency or team collaboration.
Segregation means keeping certain data sets separated from other sets of data so that you can apply specific access rules to each one. This way, based on the user role, job functions, or location, you can assign each set with the right level of access.
Structure-based segregation
This segregation type allows organizing user access based on the company’s hierarchy or structure of the organization. For example:
Top management, like admins & owners, will have full access to all system functionalities, including billing, user management, and security settings.
Departments like finance, marketing and sales, IT, HR, and so on will be granted access relevant to their department’s tasks (CRM, ERP, security configurations, setting access, etc.)
Team management may have additional permissions to approve actions, assign tasks, or generate reports.
Individual contributors may have limited access to only the tools and data they need for some specific job.
Function-based segregation
In contrast to hierarchical roles, function-based access control allows assigning permissions based on job responsibilities or actions a user performs within the system. Especially if the organization features many cross-functional teams or multi-role environments. Some examples to illustrate the results of this approach to data management:
Finance team members can issue invoices and process payments.
Customer support agents can view and manage tickets but not alter billing details.
Engineers can push updates to the system but cannot access customer data.
Security teams can monitor system logs but cannot edit business settings.
Country-based segregation
For user management in B2B SaaS companies operating globally, this segregation type guarantees compliance with laws like GDPR in the EU or CCPA in California, US. This way, operational efficiency is perfectly aligned with security. How it works in practice:
Users in different countries may only access local databases to comply with data sovereignty laws.
Some users may have restricted access to sensitive data based on regulatory differences, such as financial data access in the EU vs. the US.
Certain functionalities like payment gateways or specific third-party integrations may only be available in particular countries.
Let’s move on and explore more SaaS user account management approaches to give you an even wider range of tools for data protection and operational efficiency.
User handling on a multi-tenant application
One of the most common approaches to SaaS deployment is multi-tenancy, where a single application database and infrastructure are used to run multiple instances of customers (tenants).
Each tenant must be able to manage its users separately, securely, and reliably. Below you will find some best practices to achieve this:
Protect data against access from outside the tenant
Each customer must define the scope of its users and roles and prohibit access to its data by anyone outside the tenant. Technically, it means issuing authentication tokens like JWTs or OAuth with tenant-specific claims or/and using separate databases or schemas per tenant, depending on the architecture.
Delegate user management privileges
Different clients have different policies and procedures for user management, so instead of handling every user request centrally, SaaS platforms should allow tenant administrators to manage their own teams. This ensures that the administrators of one tenant do not have access to data in other tenants while managing the data from their tenant. In practice, this requires RBAC, scaled API keys and permissions, and tracking of all changes to user roles.
Restricting admin rights
Although all users share the same database, no admin can access data from other tenants. Within a tenant, an admin can manage authorizations, users, user groups, and other relevant settings. However, to minimize security risks, a good practice is to differentiate between system administrators and administrators at the tenant level, with only necessary permissions granted to each role.
Easy access to admin functions
Admins with the right authorizations within a tenant should not have to deal with unnecessary complexity. For example, there should be clear UI components for role assignments, permissions, and user activity logs, as well as a straightforward setup of new users with invitation-based registration and predefined role templates.
Importance of SaaS user management
SaaS adoption is growing fast across businesses of all sizes. However, without an explicit user management system, enterprises will struggle with scattered logins, redundant tools, and security risks. Let’s consider convincing factors explaining why effective SaaS user management is so important for any company.
SaaS growth
Companies expect to generate up to 50% of their revenue from launching new businesses and products by 2026. According to McKinsey, SaaS can be a precondition for this, providing access to essential software services and removing the need for in-house development. Consequently, the SaaS market itself can surge by $315 billion in 2025, rising to $1,131 billion in 2032.
Properly executed SaaS user management can help businesses catch up with such rapid growth in balancing security purposes and user experience across the plethora of applications.
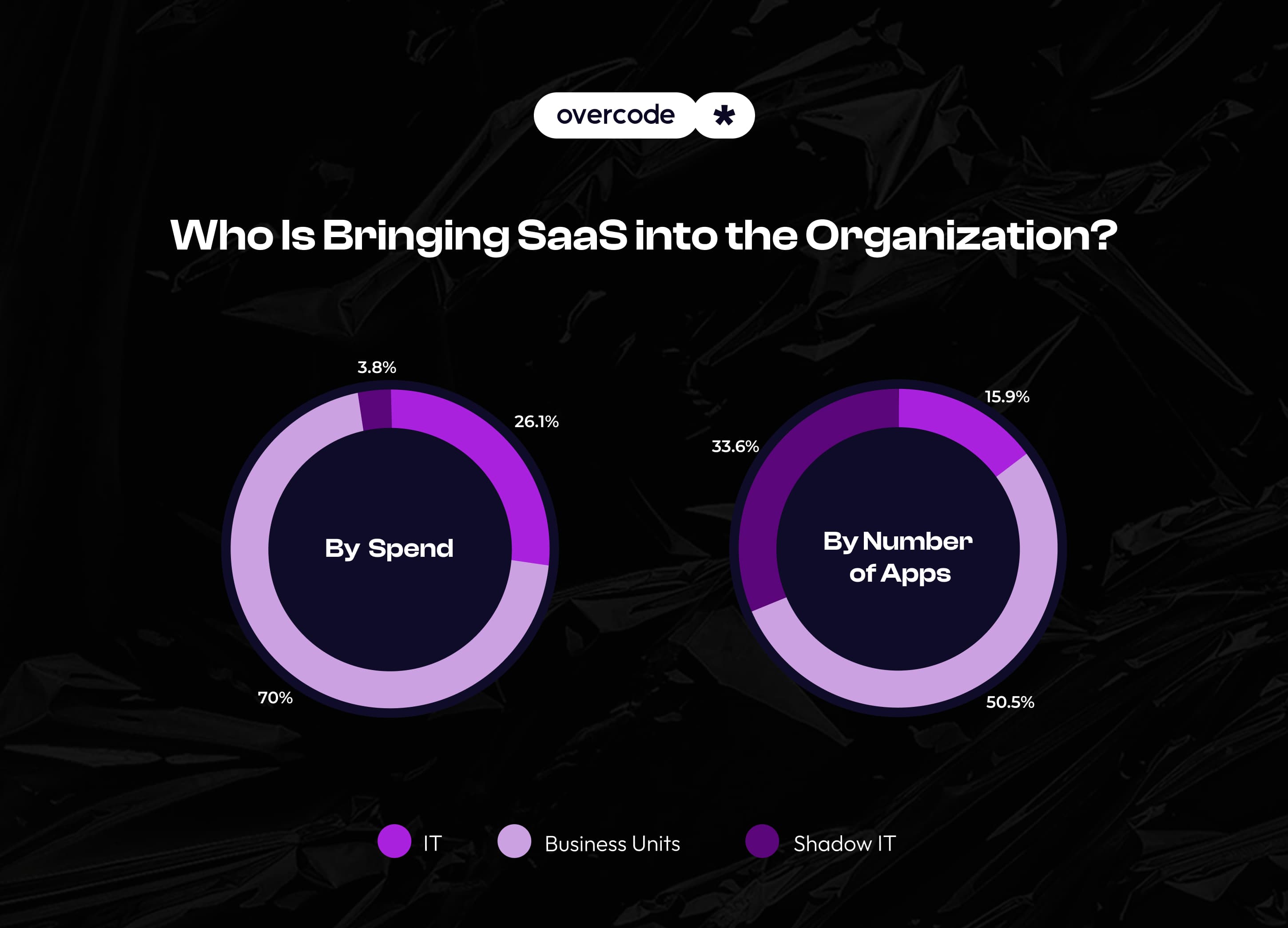
Decentralized SaaS purchasing
IT currently controls around 26% of SaaS spending and 16% of applications, while business units account for 70% of SaaS expenditure. SaaS applications purchased by individual employees make up 4% of the total spend.
Decentralization, as it’s seen, creates security risks and visibility challenges. A strategic approach to user management can help address these threats by centralized control over SaaS account management.
Replacing outdated systems
A recent survey found that 41% of European employees feel their employer is slow to adopt the latest technology, like process automation tools. On top of that, 69% believe they could provide more value if equipped with the right tools and technologies.
Effective user management software can be that necessary element to bridge the gap in the transition to modern SaaS solutions. This step can help organizations lessen heavy administrative burdens due to manual processes and inconsistent systems.
Inefficient processes
Manual user management or heavy reliance on on-premises user management systems can cost organizations considerable productivity losses. In contrast, finetuned workflows related to user onboarding, access management, and support will help business teams work more coherently and effectively.
Compliance
As we’ve discussed, compliance is critical in light of numerous data protection regulations. To meet these regulations effectively, automation is just as important as it is for operational efficiency. Luckily, many user management platforms include built-in compliance features such as tracking user activity, access controls, audit trails, reporting tools, and policy enforcement.
Implementing your user management strategy through a dedicated platform or user management as a service helps you take the reins not only over compliance but also over processes like operations, HR, and financial efficiency. More on this in the next section.
Overcode makes access control effortless with secure authentication, granular permissions, and seamless onboarding.
Need a Reliable User Management Solution for Your SaaS?
Invest in a solution that scales with your business.
Benefits of SaaS user management
A well-structured user management strategy brings organized access, security, and long-term scalability. This impact spans across departments, so let’s look closer at the benefits of SaaS user management through the lens of organizational structure.
IT department
IT teams will likely be the primary beneficiaries of SaaS user management best practices. That’s because their core responsibilities – security, access control, software management, compliance, and support – are highly dependent on effective user management.
Through centralized monitoring, IT teams can enforce security policies, track user activity, and manage access credentials effectively, considerably simplifying their jobs yet improving data protection.
Finance
SaaS spending can quickly get out of hand, especially when teams buy software independently, leading to duplicate subscriptions, unused licenses, and budget overruns. With user management software, finance teams get a clear overview of who is using what to avoid unnecessary spending, ensuring through license optimization and vendor consolidation.
Moreover, with direct access to SaaS usage data, finance managers can more accurately budget and forecast the organization’s cloud spend.
Security risks also have to do with finances. If former employees continue to have access to paid tools, this can lead to unauthorized use and compliance violations. Automated de-provisioning ensures that former employees lose access immediately, reducing financial waste and minimizing the risk of data breaches.
HR
User management software simplifies the onboarding process by automating access to the tools, allowing new hires to get up to speed faster. It helps comply with labor laws and data privacy regulations by SaaS access control to sensitive information and reducing the risk of data breaches.
In addition, HR can analyze software usage data to identify underutilized tools, allowing for better resource allocation.
Procurement
Automated SaaS user management can lend a hand to the procurement teams as long as it provides clear insights into software usage. Such knowledge can help them identify duplicate tools and reduce unnecessary costs. Procurement can work on usage data to negotiate better SaaS renewals, especially if actual usage is lower than agreed.
Plus, the software automates access controls to ensure that only authorized users can make purchases, reducing compliance risks.
Challenges of user management in SaaS applications
The upside of user management in B2B SaaS applications is now explicitly addressed. However, to avoid biased decisions, we should also look at the possible disadvantages.
Security risks
Weak passwords, reused credentials, and phishing attacks are still the biggest problems with SaaS user management. MFA helps, but many users find it cumbersome; RBAC can reduce risks, but its misconfigurations can expose sensitive data.
Concerns about user privacy
Users expect their data to be handled responsibly, as do dictated laws like GDPR, CCPA, and HIPAA. As long as SaaS platforms handle tons of personal data, it's difficult to allay privacy concerns, especially when there are compounding factors such as consent settings, weak encryption, and risky third-party integrations.
Integration and user management
SaaS applications are often integrated with identity providers, third-party authentication services, and external systems to manage user roles and permissions. Synchronizing user identities across all these platforms and systems can lead to inconsistencies, outdated permissions, and security vulnerabilities. Session management across linked applications without forcing frequent logins can also be a problem, compromising both security and usability.
Access control
It can be difficult to balance granular access control with usability, especially as the number of SaaS users grows. Incorrectly configured access controls can lead to users gaining additional privileges and access to data or features they shouldn't have. In addition, companies often grant temporary access to contractors or external partners, making security management even more complex.
User experience and adoption
According to an HBR study, improving the user experience from “poor” to “excellent” can increase profit per person hour by 45% and deliver an ROI of 150%. In contrast, a confusing user experience resulting from a rigid authentication process, for example, can drive users away. We have just made it clear how important security is in any user management application. However, the slightest inconvenience in security measures leads to end-user frustration, so balancing security and usability is a constant trade-off.
Regulatory compliance
Regulations and laws are constantly changing, making compliance a full-time job. Different regions of the world have different rules, and non-compliance can lead to fines or loss of access to certain markets. Data retention laws make regulations even more complex, requiring regular audits and compliance checks that cost time and money.
Scalability and performance
As the user base grows, the SaaS user management infrastructure may not scale well, leading to performance bottlenecks. Extensive authentication processes or access control mechanisms can also lead to latency. Remedies such as caching, load balancing, and optimized queries can help. However, if the original architecture is not scalable, fixing such issues becomes an expensive and tricky endeavor.
Data loss and recovery
Account deletions, accidental data wipes, synchronization errors, and other inadequate backup mechanisms or user data management errors can lead to the loss of user information. The result is reputational damage, compromised user trust, and a lengthy recovery process.
SaaS user management best practices
With plenty of SaaS account management best practices, we decided to group them into key areas. This structure helps assign user management tasks across your company and make sure everyone knows their responsibilities at each step.
Security measures
Enforce strong password policies: Consistently check the password requirements across SaaS systems. Demand from employees setting long, complex passwords, ideally with a passphrase of 14 characters or more. Enforce password rotation, say, every 90 days.
Use MFA: Add an extra security step in addition to user passwords: biometric authentication, hardware or software tokens, or one-time passwords sent via email or SMS.
Ensure data encryption: Use encryption methods like TLS for data shared online.
Establish session timeouts: Automatically log users out after a period of inactivity.
Elaborate a clear security policy: Make the policy available to all employees for easy reference. Conduct interviews, tests, and surveys so that the employees appreciate all seriousness of security measures and don’t take them for granted.
Develop an incident response plan: Be armed for possible security breaches by outlining counteraction steps – put down roles and responsibilities, think of communication protocols, and work out recovery procedures.
Access control
Implement an access control approach. Choose a SaaS access management model – RBAC, ABAC, or PBAC – based on your needs. See our comparison table for guidance.
Follow the Zero Trust strategy. Constantly remind employees that adherence to the least privilege access principle when using SaaS tools does help minimize security risks.
Implement time-based, one-time password tools (TOTP). You can add an extra layer of security by requiring temporary passcodes for logins.
Regularly review user permissions: For instance, plan quarterly reviews to ensure employees still need their access.
Opt for automation: Simplify user management tasks, like onboarding, offboarding, and many more.
Use hardware security keys: Set hardware keys for critical systems and/or highly privileged users.
Create a user termination process: Explicitly define steps for revoking access when an employee leaves.
Ensure EUC risk management: Require minimization of end-user computing (EUC) environments to reduce the complexity of managing multiple systems and access points.
Centralize SaaS user management: Use one platform to manage all user access through identity and access management tools. You can find plenty of IAM solutions on the market, so just for your reference, several well-tried ones:
Auth0: User management B2B SaaS with multiple security features, including MFA, SSO, and anomaly detection.
AWS Cognito: Simplifies user sign-up, sign-in, and access control; a good choice if there is a need to integrate with other AWS services.
Microsoft Entra ID (formerly Azure AD): Popular identity and access management service from Microsoft.
Frontegg: Authorization and user management platform with a comprehensive set of features.
Monitoring and auditing
Use software for insights: Look at login frequency to identify unusual behaviors that could signal a problem. Here is the outlook of the popular ones:
Okta – Provides flexible security measures and reports on login activity.
Splunk – Offers security analytics and log management.
Microsoft Entra ID (formerly Azure AD) – includes features that detect and respond to risky sign-ins and unusual access behaviors.
Keep track of user actions for audits: Implement logging to record login attempts and changes made by users. Most user management tools will spare your efforts as they have built-in logs and reporting.
Conduct regular audits: Perform audits at least twice a year to spot any access issues or anomalies.
User management and training
Provide security training for your team: Teach users about best security practices, such as not including birthdays, family names, addresses, etc., in their passwords. Hold monthly sessions on recognizing phishing attempts and protecting personal data.
Raise awareness about IT risks: For example, educate employees on the risks of connecting shadow IT to SaaS systems.
Provide thorough training to SaaS app admins. Users with privileged access should get extra training as they are the most attractive target for bad actors.
Establish a data retention policy: Decide how long to keep data and when to delete it. For example, specify that customer data is kept for four years before deletion.
Perform regular updates and patching: Set up automatic updates for all software used in your organization.
Ensure compliance: Review compliance requirements regularly to avoid penalties. Consider using SaaS application management software to get real-time insights and alerts on non-compliance and to finetune custom policies and alerting.

User management SaaS solutions at Overcode
Our clients appreciate Overcode’s adaptive approach to SaaS user management, which always accounts for the project’s specific needs. In some situations, the smartest move is to use off-the-shelf services similar to Auth-0 and AWS Cognito or integrated authentication features from Supabase and Firebase (quick example: Supabase Auth usage with React.js). Doing so can reduce the need for extensive custom coding and speed up the development.
Other times, a ready-made solution just doesn’t suit the client’s needs. If the app has unconventional user flows or specific compliance measures that standard providers don’t fully support, we suggest building a custom authentication system from scratch.
For example, using Node.js, we can manually connect the right authentication providers, ensuring every access rule, security layer, and user interaction works exactly as needed in this specific case.
Let’s refer to a couple of projects that show our expertise:
In the custom telemedicine app, we set up three distinct roles – patients, doctors, and admins – each with different permissions and access levels. Customized SaaS user management allowed the client to comply with healthcare regulations and guarantee an appealing user experience. We used AWS Cognito for that project.
For the coffee maker app, we designed a dual-role authentication system that separated coffee machine owners from device manufacturers, giving each group the tools they needed without unnecessary complexity. The client asked us to use Auth0 and Firebase.
What about the unique needs of your business?
Let’s talk to Overcode experts to find out how user management solutions can enhance the functionality of your systems.




